Are you wrestling with the complexities of managing IoT devices scattered across remote locations, especially those hidden behind firewalls that seemingly suffocate all inbound access? The truth is, securing your IoT ecosystem doesnt have to be a constant battle against impenetrable firewalls and escalating operational costs; there are solutions available.
The inherent nature of the Internet of Things (IoT) presents a unique set of challenges when it comes to securing and managing connected devices. Firewalls, while essential for protecting networks, often become obstacles when dealing with IoT devices deployed in remote environments. These devices, ranging from industrial equipment to sensors and actuators, are frequently situated behind firewalls that actively block inbound traffic, making it difficult to access them for troubleshooting, updates, or general management. The traditional approach of sending technicians onsite to connect to these devices is not only time-consuming but also adds significant complexity and cost to device management.
The rise of the Internet of Things (IoT) is transforming industries, and at the heart of this transformation are the devices themselves: light switches, thermostats, sensors, actuators, and industrial equipment. These "things" are being connected to the internet, creating a vast network of interconnected devices that generate and exchange data. This interconnectedness offers unprecedented opportunities for automation, efficiency, and data-driven decision-making.
One of the significant challenges in this landscape is the secure management of these devices. Traditional methods of securing networks, such as firewalls, can sometimes hinder access to IoT devices deployed at remote sites. Imagine trying to remotely diagnose a malfunctioning sensor in a factory or update the firmware of a smart thermostat in a distant office. The complexities of navigating firewalls and ensuring secure communication can be daunting.
However, modern solutions are emerging to address these challenges. The deployment of IoT firewalls, for example, offers a new layer of security. These firewalls are specifically designed to restrict access to IoT devices, reducing the likelihood of attackers discovering and exploiting vulnerabilities. They provide a crucial first line of defense against unauthorized access and potential cyberattacks.
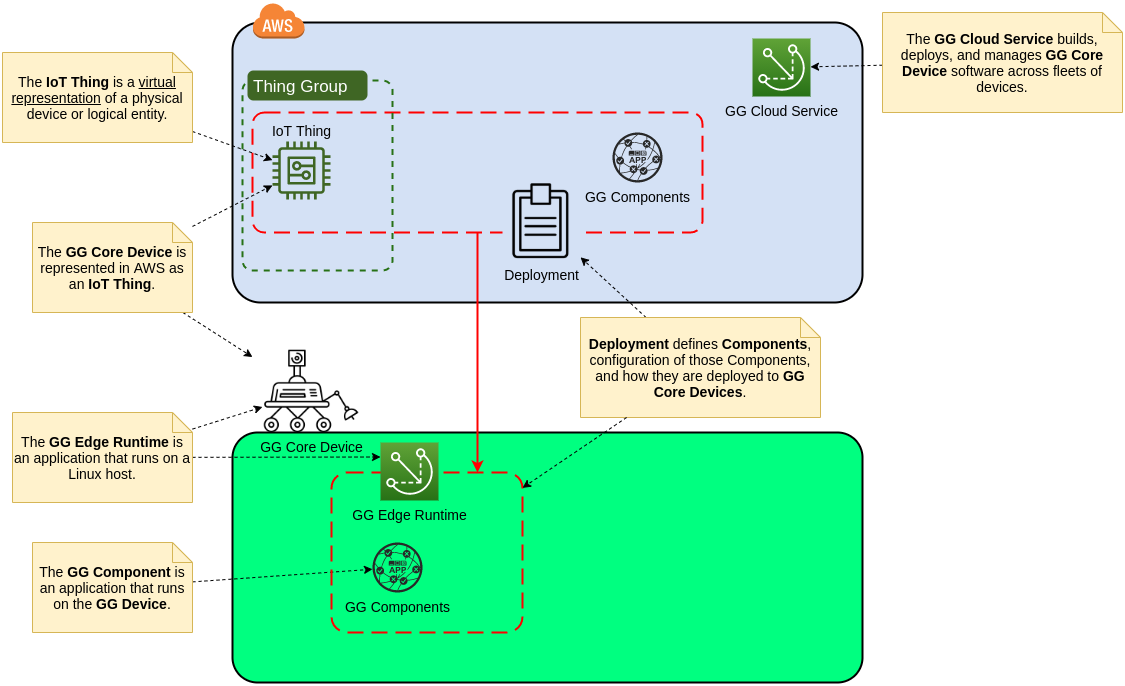
To manage these devices and ensure seamless communication, cloud services like AWS IoT Core come into play. AWS IoT Core is a fully managed service that allows devices to connect to the AWS cloud. It provides a secure and scalable platform for exchanging data and managing devices. With AWS IoT Core, developers can build IoT applications that leverage the power of the cloud to analyze data, control devices, and automate tasks.
The AWS IoT message broker is the central point to securely transmit data between devices and the cloud. It acts as a gateway, ensuring that all communication is encrypted and authenticated. Data protection in AWS IoT Core is a primary concern. AWS employs various security measures, including encryption, access controls, and identity management, to protect data both in transit and at rest.
Another significant aspect of IoT security is identity and access management. AWS IoT Core provides robust tools for managing identities and controlling access to devices and resources. This allows organizations to implement fine-grained access control policies, ensuring that only authorized users and devices can access sensitive data and functions.
Furthermore, AWS IoT Core offers compliance validation and resilience features. It has been designed to meet various industry compliance standards, making it suitable for use in regulated industries. It also provides features such as high availability and disaster recovery to ensure that IoT applications remain operational even in the event of unexpected outages.
Using AWS IoT Core with interface VPC endpoints is a technique that enhances security by allowing devices to connect to AWS IoT Core through a private network. This approach keeps traffic within the AWS infrastructure, reducing the exposure to the public internet.
Infrastructure security is another critical aspect of IoT security. AWS IoT Core incorporates various security features, such as encryption and access control, to protect the underlying infrastructure. Security monitoring of production fleets or devices with AWS IoT Core allows organizations to detect and respond to security threats in real time. It enables real-time monitoring of device activity, providing valuable insights into potential security breaches.
To ensure seamless connectivity through firewalls, it's essential to have fixed IP addresses for AWS IoT Core. These fixed IPs can then be whitelisted in the firewall, allowing IoT devices to connect to IoT Core without being blocked. The AWS IoT Core endpoint, like most AWS service endpoints, are fully qualified domain name (FQDN) entries. AWS IoT Greengrass uses the application layer protocol network (ALPN) TLS extension to enable this connection.
| Feature | Description |
|---|---|
| AWS IoT Core | A fully managed cloud service that allows connected devices to securely interact with cloud applications and other devices. |
| Firewalls | Network security systems that monitor and control incoming and outgoing network traffic based on predetermined security rules. |
| IoT Firewalls | Specialized firewalls designed to protect and manage IoT devices. |
| AWS IoT Message Broker | A central point for securely transmitting data between devices and the AWS cloud. |
| ALPN (Application-Layer Protocol Negotiation) | A TLS extension that allows applications to negotiate the protocol to be used over a secure connection. |
| FQDN (Fully Qualified Domain Name) | The complete domain name for a specific computer or host on the internet. |
| eSIM | Embedded SIM, a digital SIM that is built into a device and eliminates the need for a physical SIM card. |
For the following regions, replace with the specified region to enable all AWS services. The goal is to create a robust and easily manageable IoT ecosystem. Using AWS IoT Core provides a solid foundation for building secure and scalable IoT applications.
When implementing security measures, it's crucial to take into account the specific requirements of your devices and applications. Consider the type of data that the devices are generating, the level of security required, and the resources available to manage the devices. By carefully assessing these factors, you can create a tailored security strategy that effectively protects your IoT ecosystem.
When using device certificates for authentication, the firewall's role in inspecting and enforcing policy rules on encrypted traffic is limited. Specifically, when a device certificate is installed on a firewall to authenticate itself to a logging service or IoT security platform, the firewall cannot decrypt encrypted traffic to inspect it and enforce policy rules. For this reason, it is crucial not to attempt to use decryption policy rules on firewalls that have a device certificate installed.
To further illustrate the complexities, consider a scenario where a manufacturer of medical devices sells products to hospitals nationwide. The manufacturer's IoT application, running on AWS IoT Core, needs to receive data from these devices. Each hospital's IT department would need to be consulted to open the necessary ports (such as port 8883) in their firewalls. This requirement can become a significant administrative burden. Solutions such as whitelisting fixed IP addresses provided by AWS IoT Core can help, but they often come with additional management overhead.
The tools and resources provided by AWS are designed to help you build comprehensive diagrams and architect IoT solutions. The AWS architecture icons are simple, allowing you to easily represent the various components and services used in your diagrams. These toolkits and assets are accessible to customers and partners, enabling them to create compelling architecture diagrams that clearly communicate their IoT designs.
A notable shift is underway in telecom, with the evolution from removable physical Subscriber Identity Module (SIM) cards to embedded universal electronic circuit cards (eUICC) and Electronic SIMs (eSIMs). This transformation is driven by the surge in the Internet of Things (IoT), where devices are deployed and managed at scale. eSIM technology simplifies the process of provisioning and managing connectivity for IoT devices, making it easier to deploy and maintain a large fleet of connected devices.
As the landscape of IoT evolves, organizations are increasingly turning to innovative solutions for secure and efficient device management. Sysaid, for instance, uses AWS IoT Core and the MQTT over WebSocket secure communication protocol to manage remote software agents and overcome restricted firewall rules. This approach provides a secure and scalable way to manage and monitor remote devices, even in environments with stringent firewall policies.
The choice of communication protocol is also critical. MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol ideally suited for IoT applications. It is optimized for low bandwidth and unreliable networks, making it perfect for devices with limited resources. The use of MQTT over WebSocket Secure (WSS) adds another layer of security to the communication, ensuring that the data transmitted is encrypted and protected.
In the context of IoT, understanding the functionality and interaction between AWS IoT Core, firewalls, and security certificates are vital for maintaining a strong security posture. The combination of these technologies can ensure that your IoT ecosystem is both secure and manageable.
Consider the importance of data protection in AWS IoT Core. AWS provides various security measures, including encryption, access controls, and identity management, to protect your data both in transit and at rest. By leveraging these features, you can build a secure and reliable IoT application that complies with industry regulations.
Using AWS IoT Core with interface VPC endpoints is also an important design consideration. By using VPC endpoints, you can keep all of your traffic within the AWS network, reducing the exposure to the public internet and improving security. This approach is particularly useful for sensitive applications that require a high level of security.
Infrastructure security is a critical element in any IoT implementation. This includes the physical security of devices, the security of the network infrastructure, and the security of the cloud platform. AWS IoT Core provides a comprehensive set of security features to protect your infrastructure from threats.
Security monitoring of production fleets is an essential practice for identifying and mitigating threats. AWS IoT Core offers real-time monitoring capabilities that allow you to track the activity of your devices and detect any suspicious behavior. This proactive approach to security can help you identify and respond to potential threats before they can cause significant damage.
The AWS IoT Core endpoint is a fully qualified domain name (FQDN) entry. This entry is critical for allowing your devices to connect to the AWS cloud. AWS IoT Greengrass uses the application layer protocol network (ALPN) TLS extension to enable this connection securely.
The ability to create Amazon IoT resources and retrieve information about existing resources is vital. AWS provides tools and services that enable you to create, manage, and monitor your IoT devices and applications. You can leverage these tools to automate tasks, improve efficiency, and ensure that your IoT ecosystem is running smoothly.
IAM resources are crucial for managing access to your IoT applications. By using IAM, you can create policies that define who has access to what resources. This helps you to control access, enforce security policies, and prevent unauthorized access to your data and devices.
Accessing your AWS account ID is a fundamental step in managing your AWS resources. Your account ID is a unique identifier that allows you to access the AWS services and resources that you have subscribed to. Knowing your account ID is a prerequisite for setting up and managing your IoT applications.
The availability of AWS product icons, resources, and tools is a great asset. These resources enable you to build diagrams and create clear visualizations of your IoT architecture. By using these tools, you can simplify your architecture and communicate your design more effectively.
When choosing an IoT solution, it is crucial to consider the overall security requirements. This means looking at your data needs, the threat model, the compliance needs, and the management approach. The balance between security and convenience depends on the particular use case. By paying attention to security needs, you can make a solution that protects your IoT environment.
For IoT applications deployed in secure environments, it is essential to use a strong authentication method. This includes using certificates and advanced encryption. By using security best practices, you can keep your devices secure and your data protected.
Browse to find the icons that you need and click to download. The assets offered by AWS are valuable resources to help you streamline your design and deployment. Take advantage of these tools to help your business make the most of IoT.
Use our search to quickly find icons, and use the AWS tools that are there for your convenience to design IoT solutions to help you stay ahead of the competition.