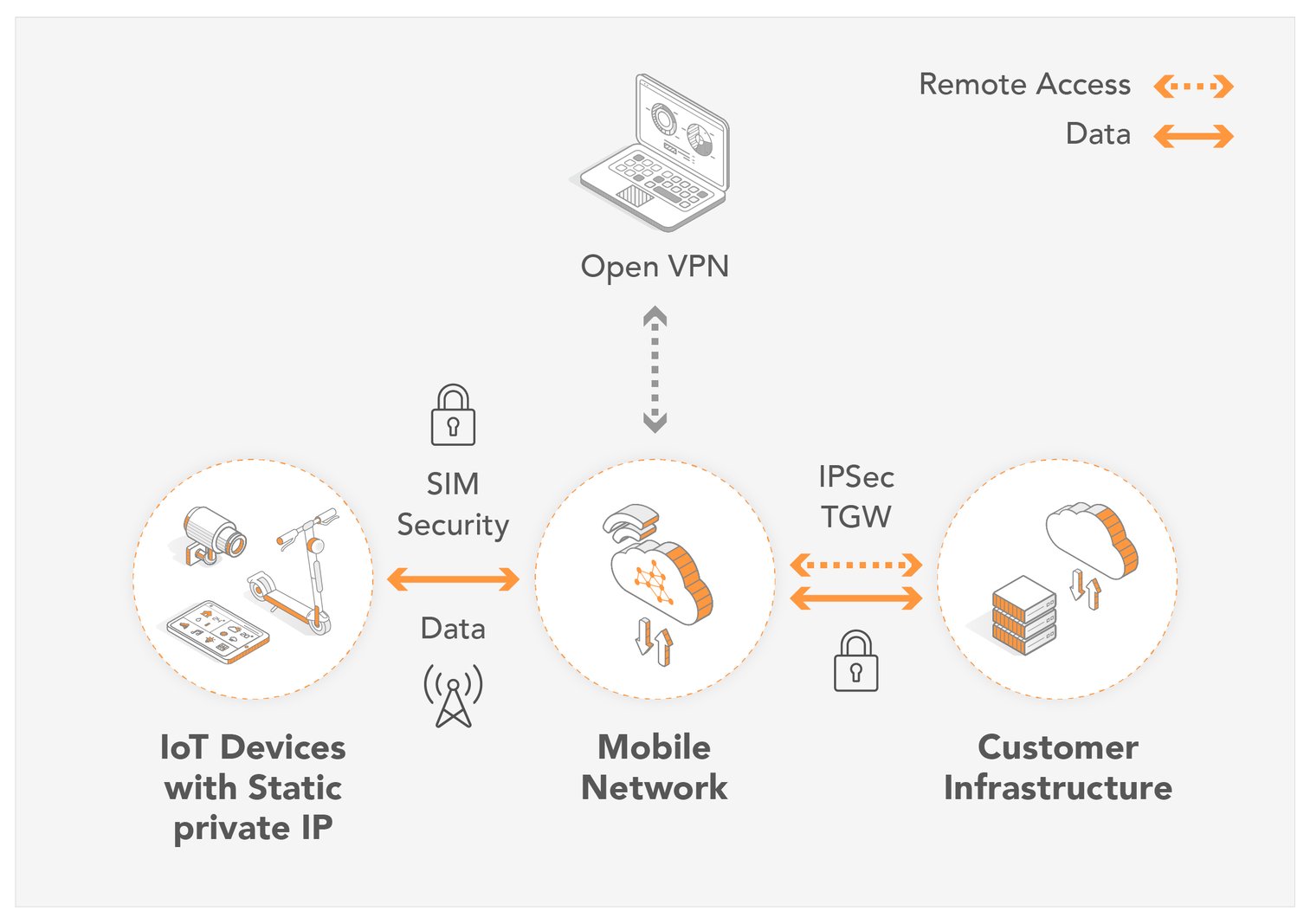
In an increasingly interconnected world, where devices communicate and operate beyond physical boundaries, the ability to remotely access, monitor, and control these "Internet of Things" (IoT) devices is not just a convenience, but a necessity.
Consider a scenario: you're managing a fleet of industrial sensors deployed in a remote, harsh environment. Or perhaps you're overseeing smart appliances in a sprawling network of homes and businesses. Without remote access capabilities, the time, cost, and logistical challenges of maintaining and troubleshooting these devices would be immense. The power to connect, configure, and debug these devices from anywhere unlocks a new level of operational efficiency and control, allowing businesses and individuals alike to reap the full benefits of the IoT revolution.
Heres a detailed look at the different facets of remote IoT device management:
What is IoT Remote Access?
IoT remote access is the capability to establish a connection with, oversee, and control Internet of Things (IoT) devices from a remote location. This crucial feature is essential for managing and supporting a wide array of IoT devices, encompassing smart appliances, industrial sensors, and connected vehicles. It eliminates the need for physical presence, enhancing operational efficiency and enabling real-time monitoring and control. This includes, but is not limited to, adjusting the temperature in your home from work or monitoring the performance of industrial equipment from a different location.
The core benefit is, therefore, to gain the ability to manage and monitor these devices regardless of the distance.
How Can You Manage Your IoT Devices Remotely?
Several methods allow for remote access and control of IoT devices. One common approach involves the use of Virtual Network Computing (VNC) clients, which allow users to connect to their IoT devices via the internet, just like connecting to a remote computer. Other methods include employing SSH (Secure Shell) connections, which offer a secure means of managing and monitoring devices, particularly useful for tasks such as debugging, configuration, and software updates.
Enhancing Security and Accessibility with VPNs
Implementing a Virtual Private Network (VPN) offers a substantial enhancement to the security and accessibility of remote IoT device management. A VPN creates an encrypted tunnel over the internet, allowing secure access to IoT devices from anywhere in the world, provided there's an internet connection. This secure connection is crucial for protecting sensitive data and preventing unauthorized access, especially when managing devices in remote locations or over public networks.
Key Strategies for Remote Device Management
1. Adoption of Centralized Management Platforms
The initial step in efficient remote IoT device management involves selecting and implementing centralized management platforms. These platforms serve as a singular point of command from which the entire control system is managed. Key features of a centralized management platform include:
- Device registration and monitoring: Centralized platforms enable the seamless registration of IoT devices, facilitating real-time monitoring of their operational status, including connectivity, performance metrics, and potential alerts.
- Remote Configuration: The ability to remotely configure and update device settings, software, and firmware is crucial. Centralized platforms simplify this process, ensuring devices are updated and configured from a central point of control, minimizing downtime and streamlining operations.
- Security Protocols: Employ robust security measures is paramount. Centralized platforms integrate security protocols like encryption, authentication, and access controls to protect devices from unauthorized access and cyber threats.
- Data Collection and Analytics: Centralized platforms collect data from various IoT devices, which is essential for generating meaningful insights and optimizing performance. These insights can aid in informed decision-making and ensure efficient operations.
2. Secure Remote Access Techniques
Securing remote access to your IoT devices involves more than just setting a password. Implementations for secure access should encompass:
- SSH: Secure Shell (SSH) is a critical tool for secure remote management and monitoring of IoT devices. It provides a secure channel for tasks like configuration, debugging, and software updates.
- VPN: Implementing a Virtual Private Network (VPN) creates an encrypted tunnel over the internet, ensuring secure access to IoT devices from anywhere in the world. This is a reliable method to access the devices securely.
3. Restricting Access to Specific IP Addresses
Limiting IoT device access to specific IP addresses or login IP within the web browser enhances security. This measure ensures that only authorized devices or users with known IP addresses can connect to the IoT devices, blocking unauthorized access attempts. Such precautions contribute significantly to the security of your IoT infrastructure.
4. Comprehensive Security Measures
Here's a comprehensive overview of crucial measures:
- Secure Authentication: Employ robust authentication methods, including strong passwords, multi-factor authentication, and regular password changes, to protect against unauthorized access.
- Encryption: Use encryption protocols like SSL/TLS to secure data transmission between IoT devices and remote access points, ensuring data confidentiality.
- Regular Security Audits: Perform regular security audits to identify vulnerabilities and address them proactively.
- DDoS Protection: Make your IoT device virtually invisible to any port scans and protect against DDoS attacks.
5. Regular Monitoring and Maintenance
Ongoing monitoring and maintenance are vital for maximizing the benefits of remote IoT device management. This proactive approach involves:
- Regular Firmware Updates: Always keep your devices up-to-date with the latest firmware versions. This addresses security vulnerabilities and enhances device performance.
- System Monitoring: Implement system monitoring tools to track device performance, identify anomalies, and receive alerts for potential issues.
- Log Analysis: Regularly analyze logs to identify security breaches, access attempts, and any other suspicious activities, which allows for immediate response and proactive mitigation strategies.
Benefits of Remote Access to IoT Devices
The benefits of remote access to IoT devices are extensive. Here are some key advantages:
- Enhanced Efficiency and Productivity: Remote access eliminates the need for on-site visits, enabling technicians to diagnose, troubleshoot, and configure devices from anywhere.
- Cost Reduction: By minimizing travel costs and on-site service calls, remote access significantly reduces operational expenses.
- Improved Security: Secure remote access methods, such as SSH and VPNs, protect devices from unauthorized access and cyber threats.
- Real-time Monitoring and Control: Remote access allows for continuous monitoring of device performance and enables real-time adjustments.
- Increased Flexibility: Remote access provides greater flexibility in managing and supporting IoT devices, regardless of physical location.
Remote Access in Action: Real-World Applications
The practical applications of remote IoT device management are vast and varied. From industrial automation to smart home control, here's how it's shaping different industries:
- Industrial Automation: Remote access enables manufacturers to monitor and control industrial equipment, optimize production processes, and troubleshoot issues without requiring physical presence.
- Smart Agriculture: Farmers can remotely monitor and manage sensors for soil conditions, irrigation systems, and weather stations, optimizing crop yields.
- Smart Home: Homeowners can remotely control smart appliances, security systems, and environmental controls, offering increased convenience and energy efficiency.
- Healthcare: Remote patient monitoring systems allow healthcare providers to monitor patients' vital signs and device usage from remote locations, improving patient care and enabling proactive intervention.
Tools and Technologies for Remote Access
Several tools and technologies facilitate remote access to IoT devices. Here's a review of the most widely used options:
- VNC (Virtual Network Computing): VNC is used for remotely controlling a device's graphical interface. Users can view and control the remote device's screen using a VNC client.
- SSH (Secure Shell): SSH is a secure protocol for accessing a command-line interface on a remote device, allowing for system administration, file transfers, and debugging.
- VPN (Virtual Private Network): A VPN provides a secure connection between the remote device and the user's device by creating an encrypted tunnel over the internet.
- SocketXP: SocketXP is a cloud-based IoT remote access and device management solution that delivers SSH access to remotely located IoT devices, providing a robust solution for management.
Advanced Considerations for Remote Access
Edge Computing
Edge computing involves processing data closer to the source, which reduces latency and bandwidth usage, and enhances real-time decision-making. Edge management is a crucial feature of remote access, enabling users to manage their devices from a single platform.
Scalability and Optimization
When dealing with numerous IoT devices, a scalable remote access strategy is crucial. It enables you to add, modify, and control devices without impacting performance, therefore optimizing efficiency. This also ensures your setup can grow in tandem with your needs.
Security Best Practices
Prioritizing security is crucial. Regular security audits, encryption, and a strong password policy provide protection against unauthorized access and ensure data safety.
Case Study: Torizon's Remote Access
Torizon's remote access provides an effective field debugging solution, empowering you to debug and configure your remote IoT devices. With an IoT remote SSH connection, you can manage and monitor your devices as if they were within reach.
In scenarios with multiple deployed devices, remote access gives valuable updates on device health and conditions, which becomes particularly useful when devices are located in dangerous or difficult-to-reach environments.
The Future of Remote IoT Device Management
The future of remote IoT device management is bright, with innovation driving continuous advancements. Here are some key trends to watch:
- AI-Powered Management: Artificial intelligence will play a significant role in automating device management, enabling predictive maintenance and enhancing security.
- 5G Connectivity: The advent of 5G will provide faster and more reliable connections, enhancing remote access capabilities and enabling more complex applications.
- Blockchain Integration: Blockchain technology will be used to enhance security, ensuring data integrity and providing secure access to IoT devices.
Conclusion
Remote access to IoT devices is an indispensable aspect of modern IoT infrastructure. It is essential for managing and supporting a wide array of IoT devices. By embracing best practices in security, implementing the right tools, and staying informed about the latest trends, businesses and individuals can harness the full potential of the IoT revolution. This remote access facilitates efficiency, boosts productivity, and ensures the seamless operation of IoT devices. The ability to connect, monitor, and control these devices from anywhere is a cornerstone of efficient modern operations.