Are you tired of being tethered to your desk, unable to remotely manage and secure your Internet of Things (IoT) devices? With Secure Shell (SSH) on your macOS, you can unlock a world of remote control and enhanced security for your IoT ecosystem, transforming the way you interact with your connected devices.
The proliferation of IoT devices in homes, businesses, and industries has created an unprecedented need for secure and efficient remote management. SSH, a robust protocol, steps in to meet this need by providing a secure and reliable method for remotely accessing and managing these devices. This article serves as a comprehensive guide, offering detailed instructions, troubleshooting tips, and best practices to ensure a seamless experience when performing an SSH login to an IoT device from your Mac. From the fundamentals of SSH and IoT to advanced configurations, we'll cover everything you need to know to manage your devices effectively, all while prioritizing security.
Before we dive into the technical aspects, let's consider why SSH is so crucial for managing IoT devices. These devices, by their nature, are often deployed in various environments and may not have the most robust security measures in place. This makes them vulnerable to unauthorized access and potential security breaches. SSH, with its encrypted communication, acts as a protective shield, safeguarding your data and ensuring secure access. By using SSH, you ensure that your IoT devices remain secure and manageable from anywhere in the world.
SSH provides several critical functionalities that make it ideal for managing IoT devices. These include:
- Remote configuration and monitoring of devices.
- Support for secure file transfers between your Mac and IoT devices.
- Encrypted communication, protecting sensitive data from unauthorized access.
- Enables remote management of IoT devices, crucial for devices lacking robust security measures.
Setting up SSH on your macOS is the first step toward remotely managing your IoT devices. It's a relatively straightforward process, but attention to detail is key to ensuring a secure and functional connection. Heres how to enable SSH on your Mac:
- Go to System Preferences.
- Click on Sharing.
- Check the "Remote Login" box.
- If necessary, click on "Allow access for:" and add users who should be able to connect via SSH.
Once you have enabled SSH on your Mac, the next step is to configure it for your IoT devices. This involves setting up SSH on the device itself and establishing a secure connection. The specific steps for installing SSH on your IoT device will depend on the device and its operating system. However, a common approach involves using a package manager or the device's built-in terminal.
Here is a general guide for connecting to your IoT device using SSH:
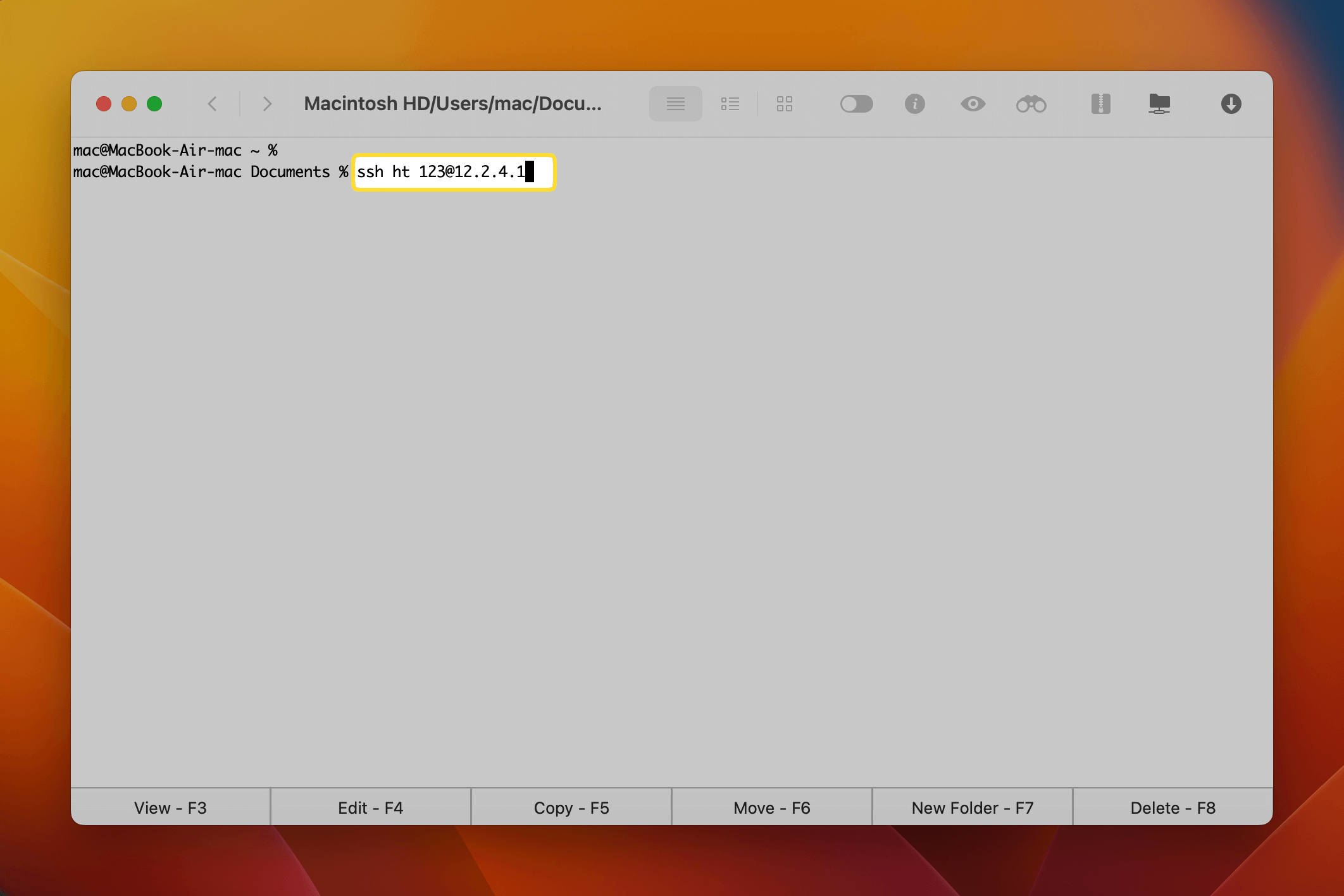
- Open the Terminal application on your Mac.
- Type the following command: `ssh username@ip_address`
- Replace `username` with the login credentials for your IoT device.
- Replace `ip_address` with the device's actual IP address.
- If prompted, enter the password for your IoT device.
- You should now be connected to your IoT device via SSH.
To make your SSH connection even more bulletproof, here are a few extra steps you can take to enhance security:
- Always use strong passwords or SSH keys: Strong passwords are the first line of defense. Consider using a password manager to generate and store strong, unique passwords for each of your devices. SSH keys offer an even more secure authentication method.
- Limit access to your IoT devices: Restrict SSH connections to trusted IP addresses. Configure your firewall to only allow SSH connections from the specific IP addresses or ranges that you use for management.
- Monitor SSH activity for suspicious behavior: Keep an eye on your SSH logs for any unusual activity. Look for failed login attempts, unexpected connections, or other red flags that could indicate a potential security breach.
Now, let's address some of the common challenges and misconceptions surrounding SSH and IoT devices. One common misconception is that SSH is too complex to set up and manage. While it might seem daunting initially, the process is relatively straightforward, and there are plenty of online resources available to help you get started. Another misconception is that SSH is only for technical experts. In reality, SSH is a powerful tool that can be used by anyone who needs to manage their IoT devices remotely. It provides a unique remote access solution that allows for very granular control of your edge devices.
Here's a breakdown of best practices to ensure a secure and effective SSH experience when working with IoT devices:
- Regularly update your IoT devices' firmware: Keeping your devices updated helps patch security vulnerabilities.
- Use a firewall: A firewall on your Mac and your IoT device can prevent unauthorized access.
- Disable SSH access when not needed: If you're not actively using SSH, disable it to reduce the risk of attack.
- Back up your configurations: Always back up your IoT device configurations to safeguard against data loss.
- Review your SSH configuration periodically: Regularly review your configuration to ensure it meets your current security needs.
As the digital landscape evolves, the significance of secure remote access to IoT devices continues to grow. SSH offers a potent solution, delivering both security and functionality to facilitate the remote management of these devices. By adhering to the principles and procedures delineated in this guide, you can confidently establish and manage SSH connections to your IoT devices, fortifying your devices against potential threats while maintaining streamlined access.
Remember, with SSH configured on your Mac, you can now connect to IoT devices. Just replace `username` with your IoT device's username and `device_ip` with its IP address. This allows you to remotely configure and monitor your devices while also protecting sensitive data from unauthorized access. It's an essential tool for anyone managing a network of IoT devices.