Are you wrestling with the complexities of managing your Internet of Things (IoT) devices, yearning for a streamlined, secure, and cost-effective solution? The ability to remotely control and manage your IoT devices, from anywhere in the world, is no longer a futuristic luxury but a present-day necessity for individuals and businesses alike.
The proliferation of IoT devices, from smart home appliances to industrial sensors, has created a landscape ripe with opportunity, but also fraught with challenges. One of the most significant hurdles is the remote accessibility of these devices. Traditional methods often involve cumbersome port forwarding configurations, the reliance on static IP addresses, or the implementation of complex and often inflexible Virtual Private Networks (VPNs). These approaches not only add layers of complexity but can also introduce vulnerabilities, leaving your devices susceptible to security threats. This guide delves into the realm of free, yet powerful, remote access solutions for your IoT devices, specifically focusing on the Secure Shell (SSH) protocol, a cornerstone of secure remote access.
Before diving into the specifics, let's address the fundamental question: What exactly is SSH, and why is it so crucial in the context of IoT device management? SSH, or Secure Shell, is a cryptographic network protocol that provides a secure channel for remote access to a network service. It establishes an encrypted connection, ensuring that all data transmitted between the client and the server is protected from eavesdropping and tampering. This makes it an ideal choice for managing sensitive IoT devices, where security is paramount. Unlike some private client tools and protocols, SSH, when implemented correctly, offers a robust defense against unauthorized access and data breaches.
The heart of effective remote IoT device management lies in the ability to monitor, control, and troubleshoot devices from a centralized location. This is particularly critical for deployments spread across various locations, behind firewalls, or operating on networks with limited accessibility. Without a reliable remote access solution, troubleshooting often necessitates sending technicians onsite, a costly and time-consuming endeavor. Moreover, the capacity to remotely update firmware, configure settings, and respond to alerts is vital for maintaining the operational efficiency and security of your IoT infrastructure.
The landscape of remote access options for IoT devices is vast and varied, encompassing both commercial and open-source solutions. One of the most compelling aspects of this field is the availability of free tools that provide a solid foundation for remote device management. These tools, often built upon the principles of SSH, offer a range of functionalities, from simple terminal access to more advanced features such as remote desktop capabilities and device monitoring. By leveraging these platforms, individuals and businesses alike can automate processes, reduce costs, and significantly improve operational efficiency.
One of the key advantages of using SSH for remote access is its ubiquity and widespread adoption. SSH is a standard protocol supported by most operating systems, making it compatible with a wide array of devices, including Raspberry Pi, Arduino, and various industrial IoT solutions. Furthermore, SSH clients are readily available for all major platforms, including Windows, macOS, and Linux. This ensures that users can connect to their IoT devices from virtually anywhere, using a familiar and user-friendly interface.
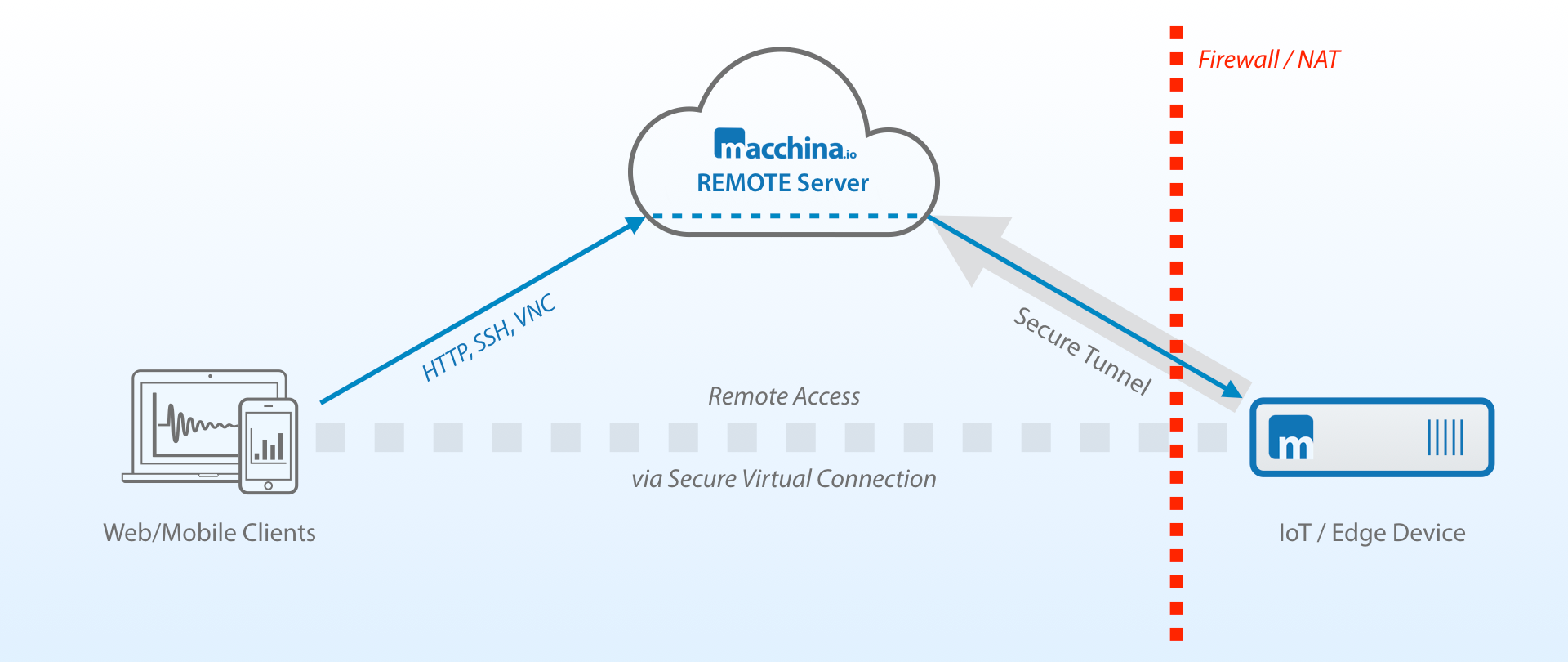
The use of firewalls is a common and necessary component in securing access to IoT devices. Firewalls act as a barrier, controlling network traffic and preventing unauthorized access. However, firewalls can also present a challenge when it comes to remote access. Traditional methods, such as port forwarding, involve opening specific ports on the firewall to allow inbound traffic. This can create security vulnerabilities and is often complex to configure. Fortunately, there are alternative solutions, such as SSH tunneling and cloud-based platforms, that bypass the need for port forwarding while maintaining a secure connection.
The process of setting up SSH remote access typically involves the following steps: First, you'll need to ensure that SSH is enabled on your IoT device. This usually involves installing an SSH server, such as OpenSSH, and configuring it to accept connections. Next, you'll need to configure your network to allow connections to the device. This may involve setting up port forwarding on your router, creating a secure tunnel, or using a cloud-based platform. Finally, you'll need to install an SSH client on your computer or mobile device. Once these steps are complete, you'll be able to connect to your IoT device remotely and manage it securely.
Let's delve into some of the most popular and effective methods for establishing SSH remote access to your IoT devices.
SSH Tunneling: SSH tunneling is a versatile technique that allows you to create secure tunnels for forwarding network traffic. One common application of SSH tunneling is to bypass firewalls that block inbound traffic. By creating a tunnel through an SSH server, you can effectively "tunnel" your traffic, making it appear as if it originates from the server itself. This eliminates the need for port forwarding and provides a secure connection to your IoT device.
Cloud-Based Platforms: Cloud-based platforms offer a comprehensive solution for remote IoT device management, often including SSH access as part of their feature set. These platforms provide a centralized interface for managing your devices, monitoring their status, and configuring remote access. They also handle many of the technical complexities, such as setting up secure tunnels and managing authentication. Some popular cloud-based platforms for IoT device management include SocketXP and Amazon Web Services (AWS) IoT.
SocketXP: SocketXP is a cloud-based IoT device management and remote access platform designed to simplify the process of managing IoT devices behind NAT routers and firewalls. It offers a user-friendly interface for remotely accessing, monitoring, and managing your devices, including Raspberry Pi fleets and Linux machines. SocketXP leverages secure SSH tunnels and eliminates the need for port forwarding, making it a convenient and secure option for remote access.
Amazon Web Services (AWS) IoT: Provided by Amazon Web Services (AWS), this platform aims to facilitate the secure and efficient management of internet of things (IoT) devices. It offers tools and features to simplify the onboarding, organization, monitoring, and updating of IoT devices at scale. Many features go beyond traditional screen sharing to include terminal access, app control, and edge management, offering a comprehensive solution to complex IoT management scenarios.
When choosing a remote access solution for your IoT devices, security should be your top priority. Ensure that the chosen solution implements strong security measures, such as SSH key-based authentication and encryption. Also, regularly update your devices and the software on your devices to patch any potential security vulnerabilities. Moreover, consider limiting access to your devices and implementing multi-factor authentication to add an extra layer of security.
In addition to security, consider ease of use and scalability. Your chosen solution should be easy to set up and use, minimizing the learning curve and the time required for configuration. Furthermore, it should be scalable, allowing you to manage an increasing number of devices without experiencing performance bottlenecks or security limitations.
Here's a simplified look at the steps involved in setting up SSH access, using `pinggy.io` as an example to create secure tunnels without port forwarding:
- Install an SSH Server: On your IoT device (e.g., a Raspberry Pi), install an SSH server like OpenSSH. This typically involves using a package manager (e.g., `apt-get install openssh-server` on Debian/Ubuntu).
- Configure SSH (Optional): You might choose to configure the SSH server with settings such as changing the default SSH port (22) to increase security, or enabling key-based authentication for added protection (strongly recommended).
- Sign up for Pinggy.io (or similar): Go to the pinggy.io website and follow their instructions to sign up for an account. Some services offer free tiers, which can be a good starting point.
- Create an SSH Tunnel: Using the `pinggy.io` service, you will typically run a command on your IoT device. This command will establish a secure tunnel, connecting your device to `pinggy.io`'s servers. The exact command will be provided by the service; it will typically look something like: `ssh -R 80:localhost:80 ssh.pinggy.io`
- Access Your Device: Once the tunnel is established, `pinggy.io` will provide you with a public URL or domain that you can use to access your IoT device from anywhere. This access will go through the secure tunnel.
These platforms empower individuals and businesses to automate processes, reduce costs, and improve operational efficiency. They offer a range of functionalities, from simple terminal access to more advanced features such as remote desktop capabilities and device monitoring. By leveraging these platforms, organizations can enhance their ability to remotely control and manage IoT devices.
In this guide, we've explored various aspects of remote access for IoT devices, focusing on the security, ease of use, and scalability of different approaches. From SSH tunneling to cloud-based platforms, the options are vast and the choice depends on your particular needs and technical expertise. Whether you're managing home automation systems or deploying industrial IoT solutions, understanding the available options is crucial.
By selecting the right tools and implementing best practices, you can confidently manage your IoT devices from anywhere, ensuring their security, reliability, and efficiency. The journey to a fully connected and controllable IoT infrastructure is within your grasp. Remember, staying informed about evolving technologies and security protocols is key to safeguarding your devices and maximizing their potential.
Here is a table that showcases a few of the tools mentioned and their main features. Please note that pricing and features can change, so always verify the most up-to-date information on the providers' websites.
| Tool | Description | Key Features | Free Tier/Options |
|---|---|---|---|
| OpenSSH (SSH Server) | A widely used, open-source implementation of the SSH protocol. A foundational tool. | Secure remote access, encrypted communication, file transfer, port forwarding. | Free and Open Source. |
| SocketXP | A cloud-based platform for remote access and device management. | SSH tunneling, remote access, device monitoring, device management, no port forwarding required. | Free plan available, paid tiers for advanced features. |
| Pinggy.io (and similar) | A service to create secure tunnels for SSH and other services. | Provides public URLs to access services running behind NAT or firewalls, easy setup. | Free tier with limitations, paid plans for more features. |
| AWS IoT | Amazon Web Services' platform for IoT device management. | Device onboarding, organization, monitoring, over-the-air updates, security features, device shadows, and more. | Free Tier available with limitations; pay-as-you-go pricing. |